P4 Code Review Submodule¶
P4 Code Review is a free code review tool for projects hosted in P4 Server. This module deploys P4 Code Review as a service on AWS Elastic Container Service using the publicly available image from Dockerhub.
P4 Code Review also relies on a Redis cache. The module provisions a single node AWS Elasticache Redis OSS cluster and configures connectivity for the P4 Code Review service.
This module deploys the following resources:
- An Elastic Container Service (ECS) cluster backed by AWS Fargate. This can also be created externally and passed in via the
cluster_namevariable. - An ECS service running the latest P4 Code Review container (perforce/helix-swarm) available.
- An Application Load Balancer for TLS termination of the P4 Code Review service.
- A single node AWS Elasticache Redis OSS cluster.
- Supporting resources such as Cloudwatch log groups, IAM roles, and security groups.
Architecture¶
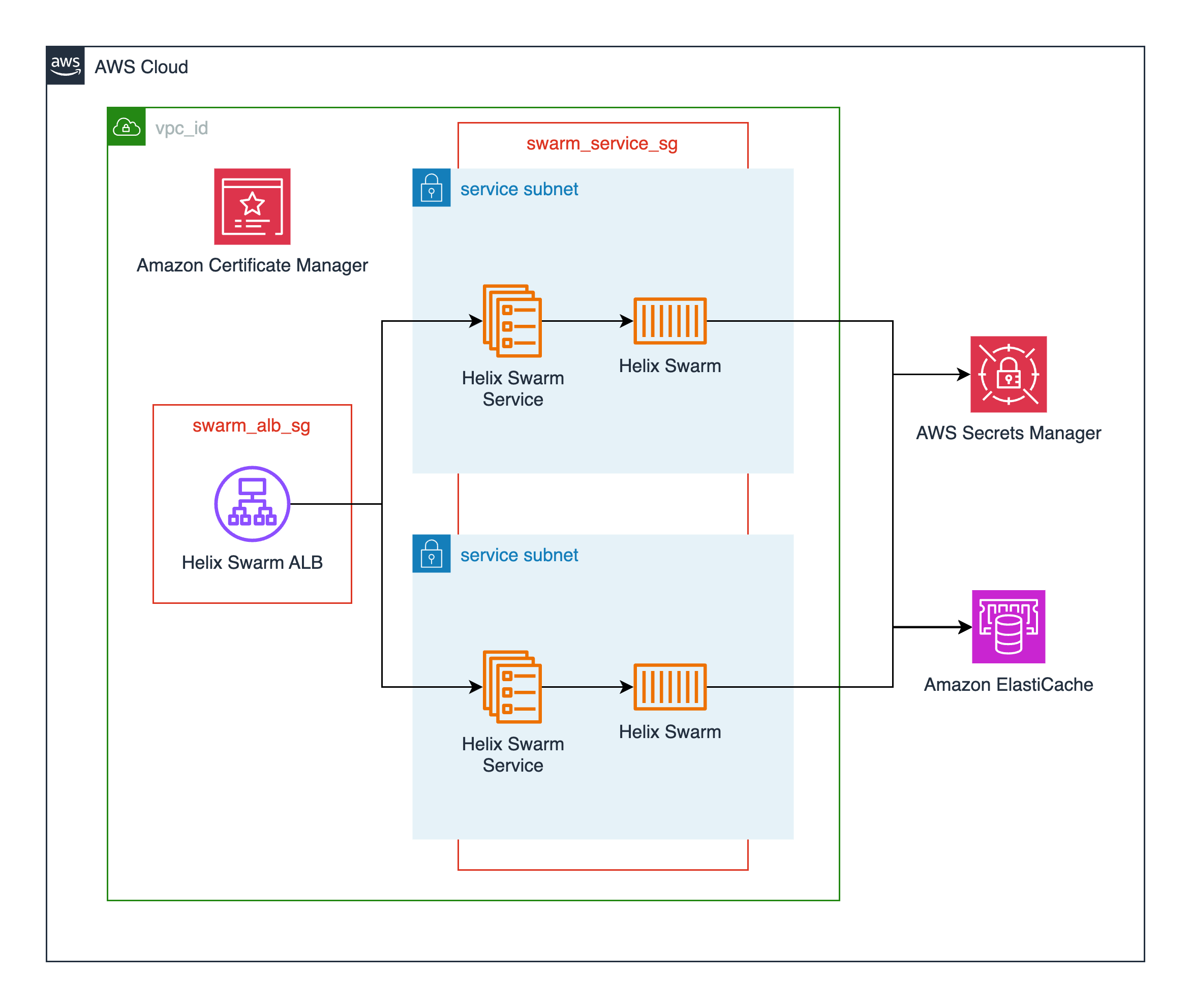
Prerequisites¶
P4 Code Review needs to be able to connect to a P4 Server. P4 Code Review leverages the same authentication mechanism as P4 Server, and needs to install required plugins on the upstream P4 Server instance during setup. This happens automatically, but P4 Code Review requires an administrative user's credentials to be able to initially connect. These credentials are provided to the module through variables specifying AWS Secrets Manager secrets, and then pulled into the P4 Code Review container during startup. See the p4d_super_user_arn, p4d_super_user_password_arn, p4d_swarm_user_arn, and p4d_swarm_password_arn variables below for more details.
The P4 Server submodule creates an administrative user on initial deployment, and stores the credentials in AWS Secrets manager. The ARN of the credentials secret is then made available as a Terraform output from the module, and can be referenced elsewhere. The is done by default by the parent Perforce module.
Should you need to manually create the administrative user secret the following AWS CLI command may prove useful:
aws secretsmanager create-secret \
--name P4CodeReviewSuperUser \
--description "P4 Code Review Super User" \
--secret-string "{\"username\":\"swarm\",\"password\":\"EXAMPLE-PASSWORD\"}"
You can then provide these credentials as variables when you define the P4 Code Review module in your Terraform configurations (the parent Perforce module does this for you):
module "p4_code_review" {
source = "modules/perforce/modules/p4-code-review"
...
p4d_super_user_arn = "arn:aws:secretsmanager:<your-aws-region>:<your-aws-account-id>:secret:P4CodeReviewSuperUser-a1b2c3:username::"
p4d_super_user_password_arn = "arn:aws:secretsmanager:<your-aws-region>:<your-aws-account-id>:secret:P4CodeReviewSuperUser-a1b2c3:password::"
}
Requirements¶
| Name | Version |
|---|---|
| terraform | >= 1.0 |
| aws | 5.97.0 |
| random | 3.7.1 |
Providers¶
| Name | Version |
|---|---|
| aws | 5.97.0 |
| random | 3.7.1 |
Modules¶
No modules.
Resources¶
Inputs¶
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| alb_access_logs_bucket | ID of the S3 bucket for P4 Code Review ALB access log storage. If access logging is enabled and this is null the module creates a bucket. | string |
null |
no |
| alb_access_logs_prefix | Log prefix for P4 Code Review ALB access logs. If null the project prefix and module name are used. | string |
null |
no |
| alb_subnets | A list of subnets to deploy the load balancer into. Public subnets are recommended. | list(string) |
[] |
no |
| application_load_balancer_name | The name of the P4 Code Review ALB. Defaults to the project prefix and module name. | string |
null |
no |
| certificate_arn | The TLS certificate ARN for the P4 Code Review service load balancer. | string |
null |
no |
| cloudwatch_log_retention_in_days | The log retention in days of the cloudwatch log group for P4 Code Review. | string |
365 |
no |
| cluster_name | The name of the cluster to deploy the P4 Code Review service into. Defaults to null and a cluster will be created. | string |
null |
no |
| container_cpu | The CPU allotment for the P4 Code Review container. | number |
1024 |
no |
| container_memory | The memory allotment for the P4 Code Review container. | number |
2048 |
no |
| container_name | The name of the P4 Code Review container. | string |
"p4-code-review-container" |
no |
| container_port | The container port that P4 Code Review runs on. | number |
80 |
no |
| create_application_load_balancer | This flag controls the creation of an application load balancer as part of the module. | bool |
true |
no |
| create_default_role | Optional creation of P4 Code Review Default IAM Role. Default is set to true. | bool |
true |
no |
| custom_role | ARN of the custom IAM Role you wish to use with P4 Code Review. | string |
null |
no |
| debug | Debug flag to enable execute command on service for container access. | bool |
false |
no |
| deregistration_delay | The amount of time to wait for in-flight requests to complete while deregistering a target. The range is 0-3600 seconds. | number |
30 |
no |
| elasticache_node_count | Number of cache nodes to provision in the Elasticache cluster. | number |
1 |
no |
| elasticache_node_type | The type of nodes provisioned in the Elasticache cluster. | string |
"cache.t4g.micro" |
no |
| enable_alb_access_logs | Enables access logging for the P4 Code Review ALB. Defaults to false. | bool |
false |
no |
| enable_alb_deletion_protection | Enables deletion protection for the P4 Code Review ALB. Defaults to true. | bool |
false |
no |
| enable_sso | Set this to true if using SSO for P4 Code Review authentication. | bool |
false |
no |
| existing_redis_connection | The connection specifications to use for an existing Redis deployment. | object({ |
null |
no |
| existing_security_groups | A list of existing security group IDs to attach to the P4 Code Review load balancer. | list(string) |
[] |
no |
| fully_qualified_domain_name | The fully qualified domain name that P4 Code Review should use for internal URLs. | string |
null |
no |
| internal | Set this flag to true if you do not want the P4 Code Review service load balancer to have a public IP. | bool |
false |
no |
| name | The name attached to P4 Code Review module resources. | string |
"p4-code-review" |
no |
| p4_code_review_user_password_secret_arn | Optionally provide the ARN of an AWS Secret for the p4d P4 Code Review password. | string |
n/a | yes |
| p4_code_review_user_username_secret_arn | Optionally provide the ARN of an AWS Secret for the p4d P4 Code Review username. | string |
n/a | yes |
| p4d_port | The P4D_PORT environment variable where P4 Code Review should look for P4 Code Review. Defaults to 'ssl:perforce:1666' | string |
"ssl:perforce:1666" |
no |
| project_prefix | The project prefix for this workload. This is appended to the beginning of most resource names. | string |
"cgd" |
no |
| s3_enable_force_destroy | Enables force destroy for the S3 bucket for P4 Code Review access log storage. Defaults to true. | bool |
true |
no |
| subnets | A list of subnets to deploy the P4 Code Review ECS Service into. Private subnets are recommended. | list(string) |
n/a | yes |
| super_user_password_secret_arn | Optionally provide the ARN of an AWS Secret for the p4d super user password. | string |
n/a | yes |
| super_user_username_secret_arn | Optionally provide the ARN of an AWS Secret for the p4d super user username. | string |
n/a | yes |
| tags | Tags to apply to resources. | map(any) |
{ |
no |
| vpc_id | The ID of the existing VPC you would like to deploy P4 Code Review into. | string |
n/a | yes |
Outputs¶
| Name | Description |
|---|---|
| alb_dns_name | The DNS name of the P4 Code Review ALB |
| alb_security_group_id | Security group associated with the P4 Code Review load balancer |
| alb_zone_id | The hosted zone ID of the P4 Code Review ALB |
| cluster_name | Name of the ECS cluster hosting P4 Code Review |
| service_security_group_id | Security group associated with the ECS service running P4 Code Review |
| target_group_arn | The service target group for P4 Code Review |